Pam Hardy Today: Unpacking Privileged Access Management (PAM) For Modern Security
Have you ever wondered about "Pam Hardy today" and what that might mean for your digital world? It's a phrase that, perhaps surprisingly, often leads to discussions about something incredibly important for keeping our online lives safe: Privileged Access Management, or PAM. You see, while "Pam Hardy" might sound like a person, in the context of cybersecurity, "PAM" stands for a whole system designed to protect sensitive information, and that's what we're going to talk about here.
It's a common little mix-up, you know, when a popular term like "PAM" gets confused with a person's name. But for anyone looking to secure their organization's most valuable digital assets, understanding what Privileged Access Management is and how it works is, quite frankly, a really big deal. So, if you're curious about the state of critical digital security measures, you're absolutely in the right spot.
This article will help clear up any confusion and show you just how vital PAM is for businesses and organizations in our connected world right now. We'll explore what it means, how it helps keep things safe, and why it's more relevant than ever for protecting against online dangers, especially today in 2024.
Table of Contents
- What is Privileged Access Management (PAM)?
- Why PAM Matters So Much Today
- How Privileged Access Management Works
- Key Benefits of Implementing PAM
- PAM in the Real World: Protecting Critical Systems
- Frequently Asked Questions About PAM
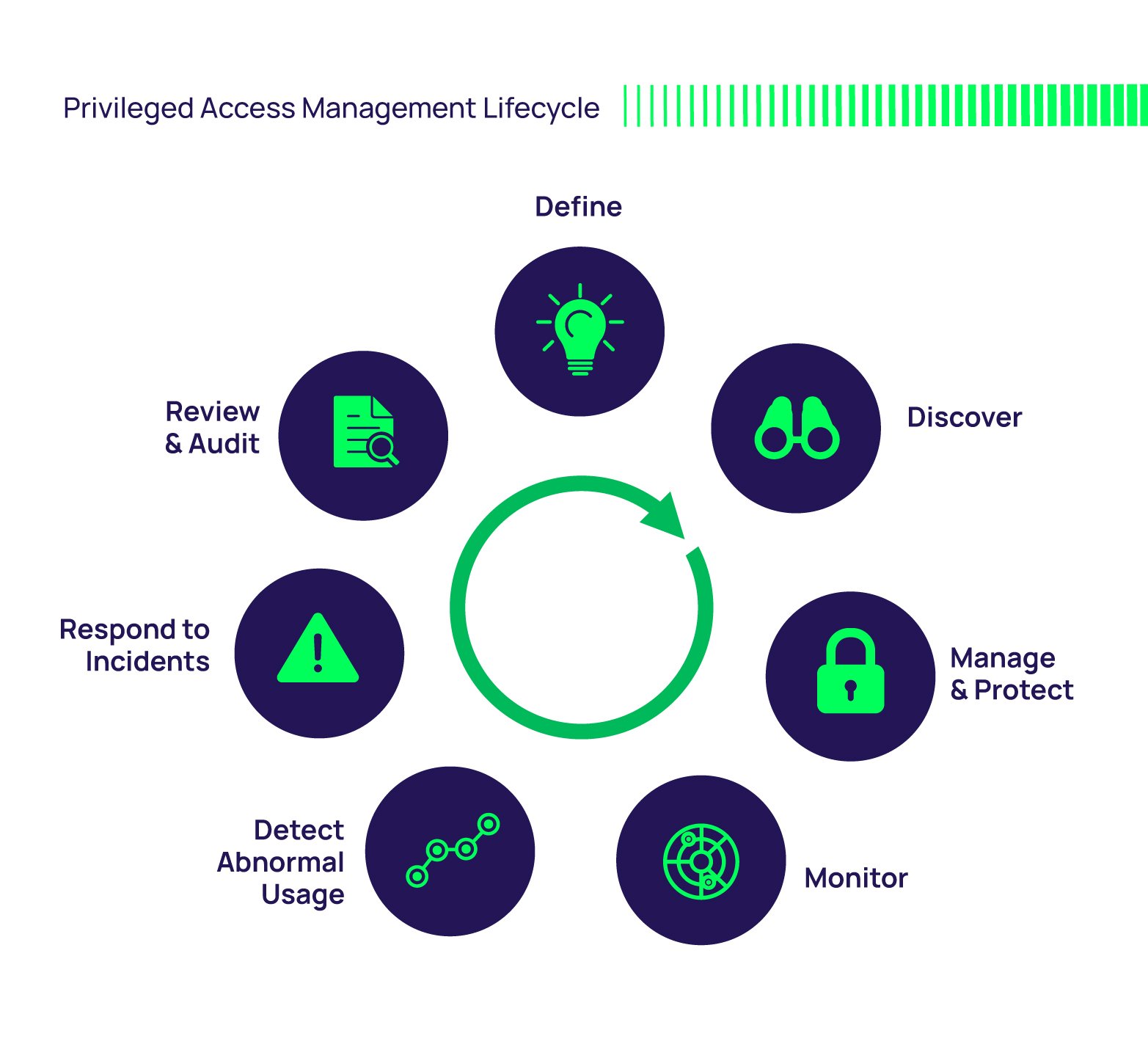
What is Privileged Access Management (PAM)?
Privileged Access Management, or PAM, is a kind of identity security solution that really helps organizations guard against cyberthreats. It does this by watching over, finding, and stopping any unauthorized actions. It's basically a very smart way to control who can get into the most sensitive parts of a computer system.
In a simple way, PAM is a cybersecurity approach and a set of technologies all working together to keep an organization's most sensitive data and really important systems safe. This is done by very carefully managing and controlling who has elevated or "privileged" access. Think of it like the master key system for a very secure building; you want to know exactly who has those special keys.
PAM is also a part of identity management and a branch of cybersecurity that really puts its focus on controlling, keeping an eye on, and protecting those special accounts within an organization. These accounts, you see, have abilities beyond what a regular user would have, so they need extra care.
Why PAM Matters So Much Today
In today's fast-moving digital landscape, where cyber threats seem to pop up constantly, having strong defenses is just incredibly important. Privileged accounts, like those used by system administrators or for critical applications, are often the main targets for attackers. If someone bad gets hold of one of these accounts, they could cause a lot of damage, maybe steal data or even shut down systems. So, PAM is a very, very crucial shield.
Without PAM, organizations are basically leaving their most sensitive doors unlocked, or at least with just a regular lock. A cyberattack could, in some respects, exploit these high-level accounts to get deep inside a network, bypassing many standard security measures. This is why PAM isn't just a nice-to-have; it's a fundamental part of a strong security plan, especially now.
The text mentions that PAM identifies the people, processes, and technology that need privileged access and then sets up policies to secure those sensitive resources. This comprehensive approach is what makes it so effective at reducing risk and helping organizations meet various compliance rules, which is, too, a big part of business today.
How Privileged Access Management Works
PAM operates through a combination of people, specific ways of doing things (processes), and technology. This setup allows organizations to truly protect their critical assets by making sure there are very strict rules about who can access privileged accounts. It's like having a highly organized security team that knows every detail.
One type, called Mim Privileged Access Management (PAM), is a solution that helps organizations limit privileged access within an existing and separate Active Directory environment. This means it can work with systems already in place, making it easier to add this layer of security without completely overhauling everything, which is, you know, really helpful for many businesses.
The system works by making sure that access to sensitive systems and data is safeguarded by carefully controlling privileged accounts. This might involve things like requiring extra authentication steps, automatically changing passwords, or only allowing access for a very limited time when it's absolutely needed. It's a bit like a temporary, highly secure pass that expires quickly.
PAM also works as an information security (infosec) mechanism that keeps identities safe, especially those with special access or abilities beyond what regular users have. It's not just about locking things down; it's about smart, controlled access that minimizes risk. So, you can see, it's quite a thoughtful system.
Key Benefits of Implementing PAM
Bringing PAM into an organization offers a whole host of advantages that really strengthen its overall security posture. One of the most important benefits is the significant reduction in the risk of data breaches and insider threats. By closely monitoring and controlling privileged accounts, companies can stop unauthorized access before it causes real trouble, which is, you know, a huge relief for IT teams.
Another big plus is improved compliance. Many industry regulations and data protection laws require strict control over who can access sensitive information. PAM systems provide the tools and audit trails needed to demonstrate that an organization is meeting these requirements, making audits a lot less stressful. This is, too, very important for avoiding hefty fines and maintaining trust.
Furthermore, PAM helps with better visibility and accountability. Every action taken by a privileged account is recorded and monitored, creating a clear log of activity. This means if something goes wrong, it's much easier to figure out what happened and who was responsible. It provides, as a matter of fact, a much clearer picture of what's happening inside the network.
For example, if you think about a utility company like Oncor, which manages critical infrastructure like power delivery, the security of their systems is incredibly important. Their competitive retailer information portal (CRIP) provides resources and tools for competitive retailers to manage their operations effectively. Protecting access to such portals and the underlying systems that handle things like damage assessment, vegetation management, and power restoration is absolutely essential. PAM helps ensure that only authorized personnel can access and modify these vital systems, preventing disruptions and protecting the public.
PAM in the Real World: Protecting Critical Systems
Let's consider how PAM applies to real-world scenarios, using some ideas from the provided text. Imagine a large utility company, perhaps like Oncor Electric Delivery, which deals with sensitive customer data and manages vital infrastructure. Their systems, like those for managing customer accounts or monitoring the power grid, need the highest level of protection. You can sign in to access Oncor Electric Delivery services and manage your account securely, but behind that login, there are many privileged accounts.
For such an organization, PAM would be critical. It would ensure that only specific, authorized personnel could access systems related to things like power restoration efforts after a winter storm, or modify settings for energy efficiency contractor portals. The text mentions Oncor damage assessment, vegetation management, and power restoration personnel working since a winter storm's arrival. These teams, you know, need elevated access, but that access must be tightly controlled and monitored to prevent misuse or external attacks.
PAM helps manage the access for various roles within such a company. For instance, the competitive retailer information portal (CRIP) provides resources and tools for competitive retailers to manage their operations effectively. Access to this, and systems that handle ESIIDs (Energy Service Identifier) or meter numbers, needs to be incredibly secure. PAM ensures that even internal users with elevated permissions can only perform actions that are absolutely necessary for their job, for a limited time, and with full audit trails.
Even things like signing up to receive alerts and status updates about power outages, or leveraging weather monitoring systems for community outreach like "Weather Current," rely on secure underlying systems. PAM helps protect the integrity of these systems, ensuring that the information provided is accurate and that the services remain available. This kind of protection is, honestly, fundamental for maintaining public trust and operational stability.
So, while the term "Pam Hardy today" might bring up thoughts of a person, its connection to "PAM" or Privileged Access Management is very relevant for understanding how organizations like Oncor keep their vital services running safely and securely. It's all about making sure that the right people have the right access, at the right time, and nothing more, which is, basically, the essence of good security.
Frequently Asked Questions About PAM
What is PAM in cybersecurity?
PAM in cybersecurity stands for Privileged Access Management. It's a type of identity security solution that helps organizations protect against cyber threats. It does this by monitoring, detecting, and preventing unauthorized access to sensitive systems and data. It's all about managing those special accounts that have elevated permissions, which are, you know, quite powerful.
Why is privileged access management important?
Privileged access management is important because privileged accounts are often the primary targets for cyber attackers. If these accounts are compromised, an attacker can gain deep access to an organization's most critical systems and data, leading to severe breaches. PAM helps to significantly reduce this risk by strictly controlling and monitoring who can use these powerful accounts, making it, in some respects, a front-line defense.
How does PAM protect sensitive data?
PAM protects sensitive data by enforcing strict controls on who can access privileged accounts and systems. It works through a combination of people, processes, and technology to safeguard critical assets. This might involve features like just-in-time access, session monitoring, and strong authentication, ensuring that only authorized individuals can interact with sensitive information, and that their actions are fully traceable. It's a very thorough approach, you see.
To learn more about cybersecurity best practices on our site, and you might also find useful information on identity management solutions.
For further general information on cybersecurity, you might check out resources from a reputable organization like the Cybersecurity and Infrastructure Security Agency (CISA).
What is Privileged Access Management (PAM)? | Delinea

Pam - cháu gái tập đoàn may mặc là em bé Việt đầu tiên có loạt ảnh đạt

Break glass privileged account